This tutorial will show you how to enable or disable Local Security Authority (LSA) protection for all users in Windows 11.
Core isolation is a security feature of Microsoft Windows that protects important core processes of Windows from malicious software by isolating them in memory. It does this by running those core processes in a virtualized environment.
Windows 11, version 22H2 supports additional protection for the Local Security Authority (LSA) process to prevent code injection that could compromise credentials.
Windows has several critical processes to verify a user’s identity. The LSA is one of those processes, responsible for authenticating users and verifying Windows logins. It is responsible for handling user credentials, like passwords, and tokens used to provide single sign-on to Microsoft accounts and Azure services. Attackers have developed tools and have abused Microsoft tools to take advantage of this process to steal credentials. To combat this, additional LSA protection will be enabled by default in the future for new, enterprise-joined Windows 11 devices making it significantly more difficult for attackers to steal credentials by ensuring LSA loads only trusted, signed code.
Reference:

What's new in Windows 11, version 22H2 for IT pros

Configure added LSA protection

New security features for Windows 11 will help protect hybrid work | Microsoft Security Blog
You must be signed in as an administrator to enable or disable Local Security Authority (LSA) protection.
LSA requires CPU virtualization turned on.
- Option One: Turn On or Off Local Security Authority (LSA) Protection in Windows Security
- Option Two: Turn On or Off Local Security Authority (LSA) Protection using REG file
- Option Three: Turn On or Off Local Security Authority (LSA) Protection using Command
- Option Four: Enable or Disable Local Security Authority (LSA) Protection in Local Group Policy Editor
- Option Five: Enable or Disable Local Security Authority (LSA) Protection using REG file
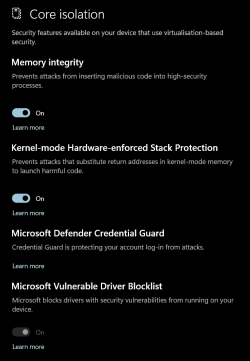
1 Open Windows Security.
2 Click/tap on Device security on the left side, and click/tap on the Core isolation details link on the right side. (see screenshot below)
3 Turn on (default) or off Local Security Authority protection for what you want. (see screenshots below)
4 If prompted by UAC, click/tap on Yes to approve.
5 Restart the computer to apply. (see screenshot below)
6 If prompted by UAC, click/tap on Yes to approve.
1 Do step 2 (on without UEFI Lock), step 3 (on with UEFI Lock) or step 4 (off) below for what you want.
This is the default setting.
(Contents of REG file for reference)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa]
"RunAsPPL"=dword:00000002
"RunAsPPLBoot"=dword:00000002When LSA is used with UEFI lock and Secure Boot, additional protection is achieved because disabling the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa registry key has no effect. It acts as a tamper protection.
(Contents of REG file for reference)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa]
"RunAsPPL"=dword:00000001
"RunAsPPLBoot"=dword:00000002If you turned on LSA with UEFI Lock using step 3, then you will need to use the Local Security Authority Protected Process Opt-out tool to remove the UEFI variable in the registry.
(Contents of REG file for reference)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa]
"RunAsPPL"=dword:00000000
"RunAsPPLBoot"=dword:000000005 Save the .reg file to your desktop.
6 Double click/tap on the downloaded .reg file to merge it.
7 When prompted, click/tap on Run, Yes (UAC), Yes, and OK to approve the merge.
8 Restart the computer to apply.
9 You can now delete the downloaded .reg file if you like.
1 Open Windows Terminal (Admin), and select Command Prompt.
2 Copy and paste the command below you want to use into Windows Terminal (Admin), and press Enter.
This is the default setting.
reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /v RunAsPPL /t REG_DWORD /d 2 /f & reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /v RunAsPPLBoot /t REG_DWORD /d 2 /fWhen LSA is used with UEFI lock and Secure Boot, additional protection is achieved because disabling the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa registry key has no effect. It acts as a tamper protection.
reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /v RunAsPPL /t REG_DWORD /d 1 /f & reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /v RunAsPPLBoot /t REG_DWORD /d 2 /fIf you turned on LSA with UEFI Lock, then you will need to use the Local Security Authority Protected Process Opt-out tool to remove the UEFI variable in the registry.
reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /v RunAsPPL /t REG_DWORD /d 0 /f & reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa /v RunAsPPLBoot /t REG_DWORD /d 0 /f3 Restart the computer to apply.
Enable or Disable Local Security Authority (LSA) Protection in Local Group Policy Editor
The Local Group Policy Editor is only available in the Windows 11 Pro, Enterprise, and Education editions.
All editions can use Option Fve to configure the same policy.
1 Open the Local Group Policy Editor (gpedit.msc).
2 Navigate to the policy location below in the left pane of the Local Group Policy Editor. (see screenshot below)
3 In the right pane of Local Security Authority in the Local Group Policy Editor, double click/tap on the Configure LSASS to run as a protected process policy to edit it. (see screenshot above)
4 Do step 5 (default), step 6 (disable), step 7 (enable with UEFI Lock), or step 8 (enable without UEFI Lock) below for what you want.
This is the default setting to allow using Option One Option Two, and Option Three.
This will override and prevent using Option One, Option Two, and Option Three.
This will override and prevent using Option One, Option Two, and Option Three.
When LSA is used with UEFI lock and Secure Boot, additional protection is achieved because disabling the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa registry key has no effect. It acts as a tamper protection.
This will override and prevent using Option One, Option Two, and Option Three.
9 You can now close the Local Group Policy Editor if you like.
1 Do step 2 (default), step 3 (disable), step 4 (enable with UEFI Lock), or step 5 (enable without UEFI Lock) below for what you want.
This is the default setting to allow using Option One, Option Two, and Option Three.
(Contents of REG file for reference)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System]
"RunAsPPL"=-This will override and prevent using Option One, Option Two, and Option Three.
(Contents of REG file for reference)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System]
"RunAsPPL"=dword:00000000This will override and prevent using Option One, Option Two, and Option Three.
When LSA is used with UEFI lock and Secure Boot, additional protection is achieved because disabling the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa registry key has no effect.
(Contents of REG file for reference)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System]
"RunAsPPL"=dword:00000001This will override and prevent using Option One, Option Two, and Option Three.
(Contents of REG file for reference)
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System]
"RunAsPPL"=dword:000000026 Save the REG file to your desktop.
7 Double click/tap on the downloaded REG file to merge it.
8 When prompted, click/tap on Run, Yes (UAC), Yes, and OK to approve the merge.
9 You can now delete the downloaded REG file if you like.
That's it,
Shawn Brink
Attachments
-
Turn_OFF_Local_Security_Authority_protection.reg684 bytes · Views: 1,092
-
Always_Enable_Local_Security_Authority_protection_without_UEFI_Lock.reg638 bytes · Views: 416
-
Always_Enable_Local_Security_Authority_protection_with_UEFI_Lock.reg634 bytes · Views: 416
-
Default_user_choice_Local_Security_Authority_protection.reg608 bytes · Views: 468
-
Disable_Local_Security_Authority_protection.reg634 bytes · Views: 589
-
Turn_ON_Local_Security_Authority_protection_with_UEFI_Lock.reg672 bytes · Views: 611
-
Turn_ON_Local_Security_Authority_protection_without_UEFI_Lock.reg672 bytes · Views: 971