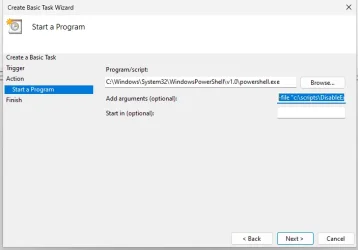
param(
[switch] $Verbose
)
function Invoke-DisableExplorer {
begin {
function Enable-Privilege {
param(
[ValidateSet(
"SeTakeOwnershipPrivilege", "SeRestorePrivilege", "SeDebugPrivilege")]
$Privilege,
$ProcessId = $pid,
[Switch] $Disable
)
$definition = @'
using System;
using System.Runtime.InteropServices;
public class AdjPriv
{
[DllImport("advapi32.dll", ExactSpelling = true, SetLastError = true)]
internal static extern bool AdjustTokenPrivileges(IntPtr htok, bool disall,
ref TokPriv1Luid newst, int len, IntPtr prev, IntPtr relen);
[DllImport("advapi32.dll", ExactSpelling = true, SetLastError = true)]
internal static extern bool OpenProcessToken(IntPtr h, int acc, ref IntPtr phtok);
[DllImport("advapi32.dll", SetLastError = true)]
internal static extern bool LookupPrivilegeValue(string host, string name, ref long pluid);
[StructLayout(LayoutKind.Sequential, Pack = 1)]
internal struct TokPriv1Luid
{
public int Count;
public long Luid;
public int Attr;
}
internal const int SE_PRIVILEGE_ENABLED = 0x00000002;
internal const int SE_PRIVILEGE_DISABLED = 0x00000000;
internal const int TOKEN_QUERY = 0x00000008;
internal const int TOKEN_ADJUST_PRIVILEGES = 0x00000020;
public static bool EnablePrivilege(long processHandle, string privilege, bool disable)
{
bool retVal;
TokPriv1Luid tp;
IntPtr hproc = new IntPtr(processHandle);
IntPtr htok = IntPtr.Zero;
retVal = OpenProcessToken(hproc, TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY, ref htok);
if (!retVal) return false;
tp.Count = 1;
tp.Luid = 0;
tp.Attr = disable ? SE_PRIVILEGE_DISABLED : SE_PRIVILEGE_ENABLED;
retVal = LookupPrivilegeValue(null, privilege, ref tp.Luid);
if (!retVal) return false;
retVal = AdjustTokenPrivileges(htok, false, ref tp, 0, IntPtr.Zero, IntPtr.Zero);
return retVal;
}
}
'@
$processHandle = (Get-Process -id $ProcessId).Handle
$typeexists = try { ([AdjPriv] -is [type]); $true } catch { $false }
if ($typeexists -eq $false) {
$type = Add-Type $definition -PassThru
}
$result = [AdjPriv]::EnablePrivilege($processHandle, $Privilege, $Disable)
if (-not $result) {
$errorCode = [System.Runtime.InteropServices.Marshal]::GetLastWin32Error()
throw "Failed to change privilege '$Privilege'. Error code: $errorCode."
}
}
}
process {
try {
# Check for Admin rights
if (-not ([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole]"Administrator")) {
Write-Warning "Must be run with administrator credentials"
return
}
try {
# Add SeTakeOwnershipPrivilege and SeRestorePrivilege for this process
Enable-Privilege -Privilege SeTakeOwnershipPrivilege
Enable-Privilege -Privilege SeRestorePrivilege
}
catch {
Write-Error $_.Exception.Message
return
}
# Set access rights on explorer.exe
try {
$NTAccount_Administrators = [System.Security.Principal.NTAccount]"Administrators"
$explorerPath = "$env:SystemRoot\explorer.exe"
$acl = Get-Acl -Path $explorerPath
$accessRule = New-Object System.Security.AccessControl.FileSystemAccessRule ($NTAccount_Administrators, [System.Security.AccessControl.FileSystemRights]::FullControl, "Allow")
$acl.SetAccessRule($accessRule)
Set-Acl -Path $explorerPath -AclObject $acl
if ($Verbose) { Write-Host "Set full control access for Administrators on '$explorerPath'." -ForegroundColor Cyan }
}
catch {
Write-Warning "Failed to set access rights for explorer.exe. Error: $($_.Exception.Message)"
return
}
# Kill explorer.exe
try {
Stop-Process -Name explorer -Force
Start-Sleep -Seconds 2
}
catch {
Write-Warning "Failed to kill explorer.exe. Error: $($_.Exception.Message)"
}
# Rename explorer.exe
try {
$timestamp = Get-Date -Format "yyyyMMdd_HHmmss"
$newName = "explorer.exe_$timestamp"
$newPath = "$env:SystemRoot\$newName"
Rename-Item -Path $explorerPath -NewName $newName -Force
Write-Host "Renamed explorer.exe to '$newName'."
}
catch {
Write-Warning "Failed to rename explorer.exe. Error: $($_.Exception.Message)"
}
}
catch {
Write-Host "An error occurred: $($_.Exception.Message)" -ForegroundColor Red
throw $_
}
}
end {}
}
Invoke-Command -ScriptBlock { Invoke-DisableExplorer }