- Local time
- 5:09 AM
- Posts
- 88
- OS
- Microsoft Windows 11 Professional High End
@neemobeer
I followed the link you provided in your recent reply. I have begun a small audit to see what more I can learn. There are so many activities to investigate. I chose the following:
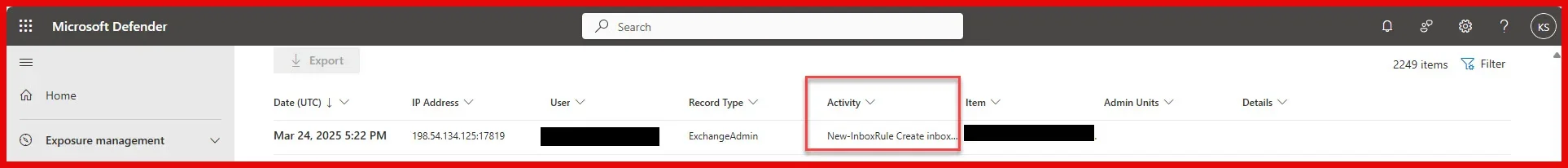
There is one thing I just remembered that I haven't mentioned before. After we unblocked and provided a new password, the user was able to send email but could not receive email. After he spoke with Microsoft, he learned that there was a rule created where his incoming email was sent or stored in conversations. Does that make any sense?
Earlier he mentioned to me that he could not receive email. Using mail trace, I knew that his emails were being delivered. He was not seeing them, though. So I had him contact Microsoft. Afterward, he mentioned that there was an Outlook rule or something to that effect. This user would not be creating Outlook rules. Again, I am not exactly sure what Microsoft did to restore his ability to have his incoming email become visible.
I followed the link you provided in your recent reply. I have begun a small audit to see what more I can learn. There are so many activities to investigate. I chose the following:
fileaccessed, filemodified, foldercopied, foldercreated, folderdeleted, managedsyncclientallowed, create, copy, mailboxlogin, mailitemsaccessed, sendonbehalf, send, update, softdelete, new-inboxrule, set-inboxrule, updateinboxrules ,
There is one thing I just remembered that I haven't mentioned before. After we unblocked and provided a new password, the user was able to send email but could not receive email. After he spoke with Microsoft, he learned that there was a rule created where his incoming email was sent or stored in conversations. Does that make any sense?
Earlier he mentioned to me that he could not receive email. Using mail trace, I knew that his emails were being delivered. He was not seeing them, though. So I had him contact Microsoft. Afterward, he mentioned that there was an Outlook rule or something to that effect. This user would not be creating Outlook rules. Again, I am not exactly sure what Microsoft did to restore his ability to have his incoming email become visible.
My Computer
System One
-
- OS
- Microsoft Windows 11 Professional High End
- Computer type
- PC/Desktop
- Manufacturer/Model
- Boxx Technologies
- CPU
- 13th Gen Intel(R) Core(TM) i9-13900K 3.00 GHz