If your user account is an Admin one you can give yourself the necessary access permissions when you get the Admin prompt challenge.
Gerry,
I am going to quibble with you because I think it will help you in the future.
Not because I am a contrary git.
All user accounts, including Admin user accounts, are initially logged in with Standard user account privileges.
If you attempt to perform a task that requires Admin privileges, a dialog box will appear.
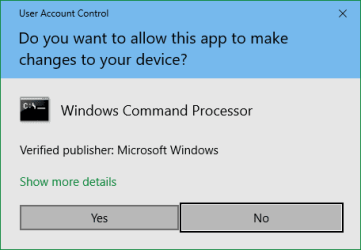
This
ConsentUI is commonly referred to as the
Admin prompt. It is also called an
ElevationUI.
You can check exactly what you are being asked to approve by clicking on that
Show more details link.
If you click on that
Yes button, you are applying your Admin privileges for that task & that task only.
Just for completeness, a Standard user account attempting to run a task that requires Admin privileges will see a slightly different dialog box that requires an Admin user account's name to be selected and its password entered.
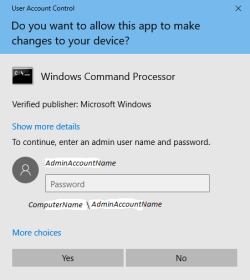
This
CredentialUI is also commonly referred to as the
Admin prompt. And it is also called an
ElevationUI.
Windows 10 introduced one exception to this rule and it has persisted into Windows 11.
An Admin user account can set a network connection as
metered in Settings, Network. There is no
Admin prompt at all. A Standard user would merely not see the option to make that setting. That's because MS are contrary gits.
All I've written here assumes you have not disabled UAC.
Change UAC Settings - ElevenForum
Since, like me & countless others, you are routinely using an Admin user account for day-to-day computing it is well worth setting UAC to its maximum setting.
- Once you've got through your initial phase of installations & setting up, you'll hardly ever get an Admin prompt anyway so you'll hardly notice the difference.
- Some years ago, there were lots of claims about malware being able to sneak past UAC's protection***. I investigated many & tested several. Despite whatever claims they made, if UAC was at its maximum level none of the malware could get through.
- - Constraining malware to merely be at a Standard user account level drastically reduces the damage it can do.
- - Malware that managed to silently achieve Admin privileges without an Admin prompt appearing could wreck your system without you seeing any indication that Admin-level actions were in progress.
If a friend of mine turned up asking to use my network I would not only check that UAC was on, I would check that UAC was at its maximum level.
*** MS never use the word
protection in relation to UAC. As far as MS are concerned, UAC is merely a convenience that allows work to continue easily without the standard user having to log off so an Admin user can log in then do the task concerned before handing the computer back to the standard user so that the standard user could then log in again and get back to doing some work [assuming they can remember what they were doing before the saga started].
And now I'm being pedantic.
You are not
the administrator.
You are
an administrator.
You can have as many admin accounts as you want.
[I have two real admin account users and two spare ones -
my ditty - Create two spare local, password-protected Admin accounts [post #2] in Windows 10, 11 - TenForums]
All the best,
Denis








